Ildikó Ernszt:[1]ICAO[1], the Core Organization of Civil Aviation - as the Main Machinery of Security? (JURA, 2007/1., 80-89. o.)
"I believe that the recommendations coming out ....
will contribute significantly
to the establishment of new standards and
far-sighted policies that will facilitate the flow
of traffic at airports, limit or avoid disruptions to passengers, and deal effectively with
threats to the safety and security of international civil aviation."
(Dr. Assad Kotaite)[2]
1. The Scope of Functions of International Civil Aviation Organization on the Field of Aviation Security
ICAO - as the central institution of international civil aviation - paid constant attention to aviation security questions since its establishment - though in the first decades it coupled with the sad phenomena of mixing professional and political matters. Besides ICAO originally concentrated on air transport business.
In the 1970s McWhinney suggests that while the newly emerging international issues exceed the frames of the competence of a specialised agency - it would be practical - because of the political character of the problems - to refer them to the appropriate organs of the United Nations - the General Assembly and the Security Council. However if the UN organs send back to ICAO to solve the problems with the justification that they relate to air transport, there would be only one solution: to " radicalise" ICAO for the challenge?
In the fight against unlawful interference of civil aviation the Council[4] of ICAO set up a Committee in the 1960s - whose task is the coordination of ICAO activity in connection with security.[5] Different standards are created in the following forms:
- Standards and Recommended Practices (SARP)s;
- Procedures for Air Navigation Services (PANS);
- Regional Supplementary Procedures - (SUPPs) and
- Guidance Material in several formats.[6] Standards and Recommended Practices appear
as the Annexes of the Chicago Convention[7], while PANS and SUPPs are procedures, rules which have not reached the level of being incorporated into Annexes. There are altogether eighteen Annexes[8] - sixteen of them deal with technological matters and belong to the Air Navigation Bureau and its sections. The remaining other two Annexes, - about Facilitation and Security -, are under the responsibility of the Air Transport Bureau.
Annex 17 deals with security matters, in 1971 a Security Manual was also published for the first time. Guidelines were set up for the Contracting Parties to make adaptation of standards more effective. Annex 17 was amended by the Council last time on 30[th] November, 2005.[9] The purpose of this amendment was to help the unified interpretation of SARPs by the member states thus easing to comply for ICAO audits. Before it was amended in November 2001[10], which contained provisions about controls in connection with national quality system of aviation security, the checking of passengers, luggage, hand luggage, the management of acts of unlawful interference in civil aviation and the significance of human resources. Other elements have also got into because of the events of 11[th] September, 2001: the use of Annex 17 for domestic flights, the information sharing relating to threats, the qualification requirements and selection of security personnel at airports, the protection of cockpit, postulates for air marshals and finally the common fight against unlawful interference in civil aviation. Annex 17 and the Security Manual are in constant review to keep up with "criminal trends."[11]
Under the aegis of ICAO several international agreements were accepted in connection with aviation security: the Tokyo Convention (1963)[12], Hague Convention (1970)[13], Montreal Convention (1971)[14], Montreal Protocol (1988)[15] and the Convention about Plastic Explosives (1991.).[16]
The necessity of creation of a new liability convention was raised to compensate the victims of unlawful acts in cases when the measure of the damage - which is caused by a criminal (often terrorist) act - exceeds the amount which is covered by the insurance of the airlines. The new convention is needed to be able to follow present trends and international legal evolution.
Besides "being the midwife" of the international conventions ICAO holds different matters in its hands from other aspects as well. E.g. following the Lockerbie incident[17] it accepted a resolution according to which member states enhance their financial, technical and material contributions to states which are in need for that. The mechanism was restarted again in 1990 - its action concentrated on four main areas.[18]
- 80/81 -
The events of 2001 called forth momentous changes in grounds of ICAO as well. The last decades proved the fact without any doubts that the quickly developing security devices are good for nothing without qualified, well-trained security personnel, experts with professional calling. ICAO pays significant attention to training - it has worked out own training programmes with regional centres.
Before only those states aggravated their security provisions which became victims of a terrorist attack - it was one of the elemental mistakes. Not even neighboring countries felt themselves in such a danger to choose the same way. Though aviation industry has special characteristics which do not "tolerate" this way of thinking - because of the already mentioned interdependency, and "if there is a weak link in the chain, then the whole chain is weak" principle. The consequence of this recognition is the close cooperation of ICAO with other international organizations and the gradual strengthening of this collaboration.[19]
On the present agenda of ICAO there is the modernization of travel documents (passports, visas), and efforts are also made to make them more secure: "the one person, one passport" concept, electronic passport, biometric identification and the introduction of "Machine Readable Travel Documents."[20] The mapping, "tracing" of newly emerging threats and elaboration on appropriate practical and legal answers means a constant task. ICAO has identified the following threats:
- use of civil aircraft as a "weapon of mass destruction",
- suicide attacks in the air and on ground facilities,
- electronic attacks: use of "radio transmitters or other means to jam or interfere with ground or airborne navigation or guidance control systems,
- computer based attacks which block or alter aeronautical communication,"
- chemical, biological attacks against passengers, misuse of nuclear and other radioactive materials,
- MANPAD attacks against aircrafts.[21]
Professor Peter St. John suggests that the problem with Western democracies and aviation industry is that security level is geared to known terrorist methods. It has the consequence that they insist on standards laid down on this way - which do not develop paralel with the achievements of criminal mind, money and technology. So governments and the industry itself applies a following tactic instead of proactive solutions.[22]
2. "ICAO Security Plan of Action"
In October, 2001 the Assembly of ICAO accepted a resolution[23] which urges the Council and the Secretary General to work out an audit programme in the interest of the security of airports. In February 2002 ICAO convened a high level ministerial conference about security of civil aviation.
On 14[th] July, 2002 at its 166[th] session the Council of ICAO announced the "ICAO Security Plan of Action". A global strategy was accepted here with the purpose of heightening worldwide security - spicing it with several guidelines and principles. It has to be applied by all member states. Regular, compulsory, systematic audits stand in the center of the action plan. During carrying out security audits the following guidelines have to be taken int consideration:
- It is inevitable to identify, analyse newly emerging threats and to work out an effective global response, to decide about time measures and make special regulations for airports, aircrafts and air navigation systems.
- The security-related provisions of the Chicago Convention and its Annexes have to be strengthened with special regard to the flight deck.
- Close cooperation and coherence has to be established on regional and subregional level.
- The results of security audits have to be proceeded on a transparent and confidential way. Besides a follow-up programme has to set up giving assistance for states to cease identified deficiencies.[24]
- It also appropriates aviation training centers - to establish a center in every region.[25]
- Training packages have to be elaborated. For 2005 this conception has also come true - on one hand the establishment of education requirements of instructors of ICAO programmes, on the other hand development of other training packages.[26]
- Newly emerging threats have to be mapped.[27]
- It urges making regulations about access to and use of passenger data.
- It anticipates working out the introduction, the requirements of the form of MRTDs.
The action programme was originally planned for the term of 2002-2004, but its execution was prolonged for the next three years in 2005.[28] Its cost was estimated for 17 million USD, the part of which - more, than 15 million USD - ICAO wants to cover from the attributions of member states. All ICAO member states, concerned international organizations were called upon to join the programme in order to achieve concrete results as soon as possible. Member states were also called on to create the financial background. It was emphasized that the realiza-
- 81/82 -
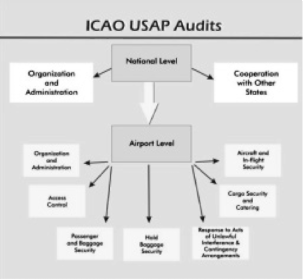
Drawing 2: Scope of Audits In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/AuditScope.htm
tion of the action plan was the common responsibility of states both in making the financial grounds and in concrete execution. The active participation of states is required in other aspects as well: in making experts and instructors available who can carry out audits, lead the courses, training programmes organized by ICAO and give assistance to states who can have direct benefit from their expertise.
3. Security Audits Under the Auspices of ICAO
The introduction of security audits stood in the heart of " Aviation Security Plan of Action". The " Aviation Security Audit Section" was set up independently in the structure of Air Transport Bureau in an organizational, management structure which is responsible for the development and execution of ICAO Universal Security Audit Programme[29],[30] Security audits monitor the ability of states to comply with the provisions of Annex 17 of Chicago Convention and how much the security system of states is in parity with the requirements on the fields of law making, national security policy, aviation authorities dealing with security matters.[31]
Audits are carried out in accordance with the following guidelines:
- Sovereignty: ICAO respects the principle that every state has exclusive authority in its airspace which includes responsibility and decisive power relating to aviation security matters and recommended changes after audits.
- Universality: audits are carried out in all member states.
- Transparency: the process of audits is made public to states.
- Timeliness: the results of audit are analysed and submitted on a timely basis to make reports.
- Consistency and objectivity: Audits are carried out in a standardized process and on a uniform way regarding their "deepness" and quality. It is assisted by the training of instructors[32], the guidelines for the whole process and the implementation of quality control system.
The monitoring team is multinational, it is leaded by a member of the ICAO Secretariat. "The multinationality" of the group is the guarantee for the elimination of favour, but it also a mean for the exchange of expertise. The process has to be conducted according to the "ICAO Codex of Behaviour" which demands that the audits should be ethical and "clean".[33]
- Fair procedure: the audited state itself has the possibility to take an active part in the monitoring process as well, to make comments, observations, remarks in connection with that in a determined time limit.
- Quality: audits are carried out by trained, qualified persons according to determined concepts, principles.
- Confidentiality: Sensitive information collected during audits is protected from unauthorized ac-cess.[34] Though ICAO urges information sharing both on bilateral and multilateral level in order to reach a mutual confidence on the level of security between states. To facilitate this, an audit report is accommodated in which the proposals - for monitored stets - are summarized.[35]
Audits are carried out both at national and airport level, so a "panoramic, comprehensive view" is given about the security potential of the state and the realization of theoretical requirements in practice as well.
Auditors value on national level if the state has the appropriate organizational and administrative structure to be able to check precisely the "security status" of its airports. International cooperation with other states is also a significant factor during supervision - which is taken into consideration. On the airport level the adequacy with Annex 17 is examined on the field of checking passengers, luggage, cargo, in flight security and catering. The action plan of the airport for unlawful and not expected interference is also monitored.[36]
4-6 months before the scheduled time of audits the monitored state is sent a "blanketta" memorandum which consists the conditions of check. A state also has to fill in a questionnaire which helps to plan the audit process. All needed information is ensured to
- 82/83 -
prepare for the next audit. Audit is carried out with the active assistance of the state - on an "opened way". The process itself takes 6-8 days[37] with the participation of 3-4 auditors. After the audit process the audited state is informed about the results of monitoring in details. The results have to be forwarded to the state within 60 days - which also has 60 days to hand in a "corrective action plan" about the elimination of deficiencies. The state - if it is necessary - can get prompt assistance in the system of ICAO. States notice their feedback about the audit process and its aspects.[38]
The follow-up evaluation, analysis of the action program worked out by the state still does not mean the end of the whole proceeding. The post-control - which is accomplished after two years - can be regarded as its final stage.
In November, 2005 ICAO strengthened the Coordinated Aviation Security Assistance and Development Programme". Its purpose is to give assistance in the elimination of deficiencies - which were discovered during audits -, to develop security infrastructure in an effective way. The strategy calls on for more effective cooperation between international organizations and states. However the programme has already its roots in the 1990s: a similar one operated in the framework of SIA Section[39]. The groups of
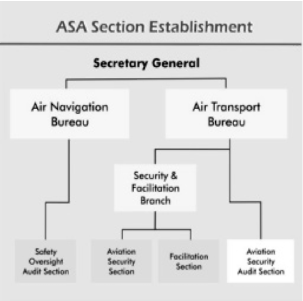
Drawing 1: Aviation Security Audit Section - Structure (ASA) In: http://www.icao.int/cgi/goto_m_atb.pl7icao/en/atb/asa/Structure.htm
guardian accompanies them and their data are recorded in the accompanying person's passport. This rule - together with other norms - is incorporated in the - already mentioned - Annex 9 of the Chicago Convention. This rule had the aim to prepare for the the section checked states which asked for a review in their aviation security provisions, and then for advise. Besides these states also needed assistance in training matters.[40] The above mentioned section worked on four main areas: giving assistance on the field of security, making surveys, coordination of aviation security programmes and organization of regional, subregional workshops.[41]
4. Securing Travel Documents
The security of travel documents also belongs to the broad theme of aviation security. Two essential interests have to be harmonized: the interest of security and the interest of simplicity: to make pre-flight checks, procedures simpler and faster.
First of all states endeavour to enforce the compliance with their legal system, whereas the airlines are out for minimalising their operational and administrative costs while rising their profit gradual. Airports try to avoid crowding, the long waiting times, passengers and cargo owners wait for the fast, clear service. The aim of harmonizing the above mentioned interests was to make the procrastination minimum, and to standardize the travel documents - which are inevitable attached to aviation - to be able to identify the passengers, cargo and airmail on a reliable way.
In certain cases terrorism, illegal migration, drug trade go hand in hand with forgery, altering and destruction of travel documents. Annex 9 of the Chicago Convention sets the standards of ICAO which must be followed when issuing documents. Its last modification came into effect in July 2005, which contained several provisions to make documents more secure. It demands their constant gradual review from the point of view of security, calls on states to keep guard on misuse of utilization and give assistance in rectification, filtering out of cases when they were counterfeited, unlawfully multiplied or passed out. Control mechanisms have to be established in order to suppress these kind of crimes. Building in biometric data is also suggested by the Annex.[42]
5. "One Person - One Passport Concept"[43]
In 1969 ICAO drew up with the suggestion that its member states should not demand a separate passport for children under the age of 16 "entering the country" - with the condition that one parent or the
- 83/84 -
exponential rise in the number of passengers and ease the scourge of issuing, renewing of passports and the administrative formalities during crossing the border.
So the entry of the spouse and the children into the common passport has become generally prevalent. But the realisation of the requirement of simplicity had an absolutely adverse effect: it only caused inconvenience for the registered persons - who did not have separate passports, and annoyance, embarrassment for border guards.
At the end of 1980s ICAO suggested for member states to abstain from issuing "common passports"[44] - though regulations which made it possible were not deleted from Annex 9, because it was considered to be too early.[45]
At the same time issuing MRTDs[46], and the standardization of personal data included in the documents were proposed. From 1990s more and more states switched over using MRTDs, paralel with this ICAO felt high time for supervision of relating rules. Its first step was to make a survey among member states. The result showed a chaotic picture: the practice of states was extremely "colorful".[47] Despite more things were proven true: on one hand present regulation does not comply with issuing requirements of MRTDs, on the other hand all states affirmed that it was possible to issue a separate passport for each person according to their domestic law. Besides other factors also urged taking further steps: not every state demanded the photo of "plus", included persons as the compulsory attachment of the passport - which can be a "hotbed" of their misuse in connection with trade and abduction of children.[48] In addition it can not be reconciled neither with the interest of the child, nor with parents if the parent/the other spouse has to travel further from the foreign country, they stay there without any identification documents. Otherwise they can not even travel without the other party, the passport holder...
In 2002 Annex 9 was amended: independently of the age of the concerned person, everyone should have a separate passport.[49] In the interest of reducing the increased cost of families several proposals were born.[50]
6. MRTDs
Machine Readable Travel Documents contain data which are readable, detectable by human eyes and machines. ICAO is invested with the possibility of issuing MRTDs by Chicago Convention - when it obligates member states to accept internationally assumed standards in connection with migration, customs and other matters.[51] Rules were worked out by Technical Advisory Group dealing with the topic of MRTD.
At present passports, visas and other official travel documents are issued in this format. In standardised format all MRTDs include the compulsory identification data of the holder, a photo (or a digital picture) in two lines in a special style[52] - which can be detected by a machine as well. It makes possible for properly configured reading machines to be able to interpret all kind of documents issued by any state. The "goal formula" is quite simple: to be able to identify anybody, anywhere, from any country with total assurance. Document 9303 issued by ICAO contains special requirements for MRTDs in three parts: for passports, visas and other official travel documents.[53]
Today more than 110 countries use or plan issuing MRTD passports. States were given a time limit - April 10, 2010 - within MRTDs have to be issued. ICAO accepted a special project in giving assistance for switching to issuing MRTDs: it can manifest in training, planning, giving financial assistance, project management or system evaluating services.[54]
7. Biometric Identification
Applying biometrics means the statistical analysis of biological characteristics. Biometrics can be physical features: the eye, face, hand, voice, or behaviour like the rhythm of signature or typing.[55]
Biometrics mean the highest security level among all possible means.[56] Their history goes back to ancient times. First they existed in a quite simple form: at the time of Egyptian pharaohs the height was measured, in ancient China drawings were made about fingers. Automatic identification appeared first at maximum security, top secret institutions. From 1960s firms also started to apply these security devices.[57] FBI started automatic identification with the help of fingerprints also at this time which became widespread for the 1970s. Later human eye - iris and retina - also appeared as a biometric, the use of face and "dynamic signature" for this purpose is a recent phenomena.
The eye means the highest security level of bio-metric identification, it is absolutely unique in the case of every person. Identification is carried out by virtue of iris or retina. Iris is in direct connection with brain, so the "re-use" of a deceased person's eye is nearly impossible. Security can be heightened, if not only the drawing of iris is checked, but also the natural pupillary notion and unique refractions for infra red lights are tested. Probably the uniqueness of
- 84/85 -
this kind of information results in the lowest false accept among all biometrics. Further iris can be scanned from some metres as well, so the tested person does not feel the procedure intrusive and humiliating.
Identification by retina - besides by iris - is considered to be the most secure, but also the most intrusive procedure. The person - which has to be identified - has to put his chin in some centimetre distance from the machine for identification and has to concentrate on a green dot. It is only applied in top secret institutions.[58]
Face recognition systems test the unique features and their position on face. In fact it is the most ancient, most natural biometric, since that is the way mankind can identify its members, it is the key of identification. Extremely complicated softwares are needed in case of this kind of systems. What is more face can be altered relatively easily: a moustache, a beard, glasses, wrinkles appearing through years conjure an absolutely new person in front of us. Besides we should not forget about the wonders of plastic surgery either. So application of these systems does not mean as high level security as in case of eyes.
Two methods are used: creating video- or thermal images.[59] In case of face - recorded by video- the position of several points are mapped, basically the position of eyes and mouth. Of course the 3-D record makes possible a much more secure identification by recording more points. While "shooting" the so called thermal images by thermal cameras the thermal image of the face is "traced" - with the help of vascular system. It is an important drawback that this procedure is a more expensive solution.[60]
Fingerprint is one of the most common bio-metric.[61] It is widely accepted that there are no two identical fingerprints - not even identical twins are exceptions. The thorough, systematized analysis of fingerprints started in the 1800s: since then there were several positive and negative feedback in connection with that.[62] Its disadvantage is that its use is associated with criminality, it conveys a degrading impression. Besides the quality of fingerprint is affected by the stage of skin, blood pressure and impurities.[63] Further the geometry of hand, fingers, palm print[64] , signature and voice can also have significance as biometric. A 3D image is shot about the hand in which the length, shape of fingers, joints, phalanxes are measured - it is not the most secure method, but it is often used because of its convenience and speed.[65]
Analysis of sound is based on mapping of the characteristics of the vocal tract. Its danger derives from the deficiencies of poorly designed speaker verification system and the possibility of their misuse. It is much more reassuring if they are combined with other methods.
To the biometrics of the future belong the odour of human body, DNS analysis, the vascular system, and the emitted frequency of certain organs.[66] Though not all biometric is appropriate for building into MRTD travel documents. In 1999 the Technical Advisory Group of ICAO initiated a research about their compatibility. According to the study on the field of aviation the face, fingerprint and iris can be considered to be a biometric.[67]
Security embraces a wider spectrum in this regard: not only the physical document, its characteristics, but also the process of issuing, authentication - which get into focus more and more. Events of 11 September, 2001 are the most typical examples of the fact that the security of issued documents does not mean a total protection against crimes: incompetent persons can have unauthorized access to lawfully issued documents. Biometric identification doubles security: on one hand the control of document, on the other hand that of identification criteria. It simplifies and makes identification of passengers faster at border control: automatic devices can be applied which compare the data included with the identification features of the passenger in front of them which does not take more time than some seconds. If the identification is unsuccessful, security personnel can make the secondary control.[68]
We should not forget about identification of security personnel of airports either - biometrics are appropriate for this purpose as well. In several countries pilot programmes were launched to study the possibility and practicability of biometrics. In Japan, Australia and in the Netherlands tentative projects were started in which the interoperability of biometric devices comes to light besides their justification.[69] According to an idea pilots would get a chip card after getting their licence which includes this kind of special identifiers as well. They could get into cockpit or to strictly guarded areas inside of airports with the help of this card. Applications of biometrics for this purpose have already their examples at the airports of the world and it is more and more widespread.[70]
There are reasons for and against of biometrics. More experts raise that the procedure is quite expensive and does not mean a total security. It is absolutely true: One technology is not enough in itself, a lot more is needed. However this technology is getting cheaper and cheaper, and more and more often it is used. Who are opposed to this new method refer to the possible mistakes and misidentification.[71] Nevertheless it is more feasible that the authorized person is held back than the converse possibility. Besides we are the witnesses of an unbelievable, drastic technical development on this field. Finally serious doubts emerged in the area of Human Rights.
- 85/86 -
8. Like the Shadow...
Applying biometrics is a kind of redefinition of human body - and its treatment as information. Finally let me quote the words of Irma van der Ploeg about emerging doubts: "Who you are, how you are, and how you are going to be treated in various situations, is increasingly known to various agents and agencies through information deriving from your own body, that is processed elsewhere, through the networks, databases, and algorithms of the information society. Once translations of bodily characteristics into electronically processable data have been made, these bodies become amenable to forms of analysis and categorization in ways not possible before. The biometrically identified bodies at an airport immigration booth are automatically assessed as either known or unknown, legal or illegal, wanted or unwanted, low or high security risk - assessments with very concrete consequences for the persons concerned. Particular profiles can be produced from large amounts of data, and social identities affixed to persons behind their backs, whether they actually fit the category in question or not. With the growing interconnectedness of networks, cross-matching of databases, and sharing of information between agencies and institutions, both in public and private sectors, such attributed identities can become like a person's shadow: hard to fight, impossible to shake."[72]
Literature
Aleman, M. A.: Strengthened Aviation Security Branch Oversees Newly-Developed Assistance Programme, ICAO Journal, Vol. 45, No. 6., June 1990
Atkinson, Robert D.:Aviation Security System for 21[st] Century Must Fully Incorporate Latest Technologies, ICAO Journal, Vol. 57 No. 5., June 2002
Bhanot, M. L.: A Matter of the Highest Priority, ICAO Journal, Vol. 50, No. 10., December 1995
Gilenson, Hughes: Holistic Approach to Document Security Beginning to Take Hold In: ICAO Journal, Vol. 59 No. 7., October 2004
Huopio, Simo: Biometric Identification, authorization and Access Control in Open Network Environment, http://www.tml.tkk/fi/Opinnot/Tik-110.501/1998/papers/12biometric/biometric.htm
McWhinney Edward Q.C., Aerial Piracy and International Terrorism, The Illegal Diversion of Aircraft and International Law, 2[nd] revised edition, Martinus Nijhoff Publishers, Dordrecht/Boston/Lancester 1987
Poyner, Alan: Industry Focuses On Developing Training
Material That Will Improve Global Security Effort ICAO Journal, Vol. 51, No. 9., November 1996
Van Der Ploeg, Irma: Biometric Identification Technologies: Ethical Implications of the Informatization of the Body, Biometric Technology and Ethics, BITE Policy Paper No. 1, March 2005 In: www.danishbiometrics.org/admin/files/policy_paper_1_july_version.pdf
Yfantis, Konstantinos N., Applications of Biometrics Implications for Security and Ethics, University of Illionis at Urbana - Champaign, November 13, 1997, http://www.staff.uiuc.edu/~efantis/biometrics/sld001.htm
Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006
Safety and Security: In the Aftermath of 11 September, ICAO Resolved to Strengthen Aviation Security Worldwide ICAO Journal, Vol. 57, No. 6., July-August 2002
Convention on Offences and Certain Other Acts Committed on Board Aircraft, signed at Tokyo, on 14 September 1963
Convention for the Suppression of Unlawful Seizure of Aircraft, Signed at the Hague, December 16., 1970
Convention for the Suppression of Unlawful Acts Against the Safety of Civil Aviation, signed at Montreal 1971
Convention on the Marking of Plastic Explosives for the Purpose of Detection, signed at Montreal, 1 March, 1991
Protocol for the Suppression of Unlawful Acts of Violence at Airports Serving International Civil Aviation (1988), Supplementary to the Convention for the Suppression of Unlawful Acts Against the Safety of Civil Aviation, signed at Montreal 24[th] February 1988
Resolution A33-1: Declaration on misuse of civil aircraft as weapons of destruction and other terrorist acts involving civil aviation
Auditor Training and Certification In:http://www.icao.int/cgi/goto_m_atb.pl?
http://www.icao.int/cgi/goto_m_atb.pl7icao/en/atb/asa/ConfidBiometrics Deployment of Machine Readable Travel Documents, ICAO TAG MRTD/NTWG, Technical Report, Development and Specification of Globally Interoperable Biometric Standards for Machine Assisted Identity Confirmation Using Machine Readable Travel Documents
http://www.icao.int/mrtd/down is load/documents/ Biometrics deployment of Machine Readable Travel Documents 2004.pdf, 21 May 2004, Biometric Selection Report, TAG, February 2002entiality.htm
International Civil Aviation Organization, First Meeting of Directors of Civil Aviation of the Caribbean Region, CAR/ DCA/1, WP/19, 10/9/02
www.icao.int/icao/en/ro/nacc/meetings/2002dcacar1/cardca1-wp19.pdf
ICAO recommendations confirm move towards biometric identification and passenger record transfer http://ec.europa.eu/idabc/en/document/2401/364
The ICAO USAP Principles In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/USAP_Principles.htm
http://www.icao.int/cgi/goto_m_atb/fal/Passport_concept.htm "One Person, One Passport Concept"
The Audit Process In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/Process.htm
Major Accomplishments Under the ICAO Aviation Security Plan of Action, http://www.icao.int/avsec/index.asp
Aviation Security Audit Section - Structure (ASA) http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/Structure.htm
http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/AuditScope.htm
http://www.icao.int/cgi/goto_m.pl?icao/en/anb/mais/index.html
http://www.icao.int/atb/avsec/indexs.asp?static=annexe17 ■
NOTES
[1] International Civil Aviation Organization, further: ICAO
[2] The former President of the Council of ICAO. In: ICAO recommendations confirm move towards biometric identi-
- 86/87 -
fication and passenger record transfer http://ec.europa.eu/idabc/en/document/2401/364
[3] McWhinneyl Edward Q.C., Aerial Piracy and International Terrorism, The Illegal Diversion of Aircraft and International Law, 2nd revised edition, Martinus Nijhoff Publishers, Dordrecht/Boston/Lancester, 1987. p 132
[4] The structure of ICAO consists of Assembly, Council, Secretariat and other organs which become necessary.
[5] Besides several Assemblies were also held, which had extreme importance in connection with our topic: in 1968, 1970, 1971 and in 1973. There are Assemblies in every three years: in 1970 and 1973 extraordinary sessions were convened - with a special topic. In: Bhanot, M. L.: A Matter of the Highest Priority, ICAO Journal, Vol. 50, No. 10., December 1995, p 5.
[6] http://www.icao.int/cgi/goto_m.pl7icao/en/anb/mais/index.html
[7] Convention on International Civil Aviation, Dec 7, Further: Chicago Convention
[8] Annex 1: Personnel Licensing, Annex 2: Rules of the Air, Annex 3 : Meteorological Service for International Air Navigation, Annex 4: Aeronautical Charts, Annex 5: Units of Measurement to be Used in Air and Ground Operations, Annex 6: Operation of Aircraft Annex 7: Aircraft Nationality and Registration Marks, Annex 8 Airworthiness of Aircraft, Annex 9: Facilitation, Annex 10 Aeronautical Telecommunications, Annex 11: Air Traffic Services, Annex 12: Search and Rescue, Annex 13: Aircraft Accident and Incident Investigation, Annex 14: Aerodromes, Annex 15: Aeronautical Information Services, Annex 16: Environmental Protection, Annex 17: Security: Safeguarding International Civil Aviation Against Acts of Unlawful Interference, Annex 18: The Safe Transport of Dangerous Goods by Air. In: http://www.icao.int/
[9] It became effective from 10th April 2006. It became applicable from July 2006. In: http://www.icao.int/atb/avsec/indexs.asp?static=annexe17
[10] Its 10th amendment came into effect in July 2002.
[11] Safety and Security: In the Aftermath of 11 September, ICAO Resolved to Strengthen Aviation Security Worldwide ICAO Journal, Vol. 57, No. 6., July-August 2002, p 33.
[12] Convention on Offences and Certain Other Acts Committed on Board Aircraft, signed at Tokyo, on 14 September 1963
[13] Convention for the Suppression of Unlawful Seizure of Aircraft, Signed at the Hague, December 16., 1970
[14] Convention for the Suppression of Unlawful Acts Against the Safety of Civil Aviation, signed at Montreal, 1971
[15] Protocol for the Suppression of Unlawful Acts of Violence at Airports Serving International Civil Aviation (1988), Supplementary to the Convention for the Suppression of Unlawful Acts Against the Safety of Civil Aviation, signed at Montreal 24th February 1988
[16] Convention on the Marking of Plastic Explosives for the Purpose of Detection, signed at Montreal, 1 March, 1991
[17] In 1988 two agents of the Lybian secret agency blew up the flight of the American PanAm Airlines above the Scottish village, Lockerbie - causing nearly the death of 300 persons.
[18] Giving advise in connection with aviation security organizations and techniques, carrying out test, controls, coordination of aviation security programs, trainings, organisation of seminars and conferences on regional and subregional levels. In consideration of its success its duration was extended by the Assembly of ICAO till 1998. In: Bhanot [p] [6.] 19
[19] ICAO extremely strengthened its cooperation with the aim to fight against the unlawful interference in civil aviation with the following international organizations - which can be considered to be key institutions in this area: INTERPOL, (ICPO/International Criminal Police Organization), UPU/Universal Postal Union, IATA (International Air Transport Association), ACI/Airports Council International, and with IFALPA (International Federation of Air Line Pilots' Association). In: Bhanot p 7
[20] further MRTDs
[21] Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006, p 26.
[22] Professor St. John stated the above mentioned thoughts in his book with the title "Air Piracy, Airport Security and International Terrorism" in 1991. In: Poyner, Alan: Industry Focuses On Developing Training Material That Will Improve Global Security Effort ICAO Journal, Vol. 51, No. 9., November 1996 p. 5
[23] Resolution A33-1: Declaration on misuse of civil aircraft as weapons of destruction and other terrorist acts involving civil aviation
[24] International Civil Aviation Organization, First Meeting of Directors of Civil Aviation of the Caribbean Region, CAR/DCA/1, WP/19, 10/9/02, In: www.icao.int/icao/en/ro/nacc/meetings/2002dcacar1/cardca1-wp19.pdf
[25] Training centers were established at 15 places in the following cities: Amman (Jordan), Auckland (New-Zealand), Brussels (Belgium), Buenos Aires (Argentina), Casablanca (Morocco), Dakar (Senegal), Hong Kong (China), Johannesburg (South African Republic), Kiev (Ukraine), Kuala Lumpur (Malaysia), Kunming (China), Moscow (Russian Federation), Nairobi (Kenya), Port of Spain (Trinidad and Tobago), Quito (Ecuador). So there are training centers in every region, subregion of the world lectures and there is security related education in all official languages of ICAO. In: Major Accomplishments Under the ICAO Aviation Security Plan of Action, http://www.icao.int/avsec/index.asp 1.1.c) point
[26] More than 50 programs are available in training centers in a year. The programs for national inspection, hostage negotiations (on two levels) have been developed recently. ibid. d), e) points
[27] ICAO have urged the Council and Secretary General in its A33-1 resolution to map the newly emerging threats to international civil aviation with special regard to the present conventions. it was stated that they were not able to cover new threats any more - most countries agreed on with this statement. ibid. 3.1.a) point
[28] ICAO determines its working plans for three years.
[29] USAP
[30] Aviation Security Audit Section - Structure (ASA) http://www.icao.int/cgi/goto_m_atb.pl7icao/en/atb/asa/Structure.htm
[31] In 2005 61 audits were carried out, the number of checked, monitored countries reached 105. In: Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006, p 25
[32] In 2005 auditor trainings, courses were conducted in Buenos Aires, Kuala Lumpur and in Oklahoma City, so there are altogether 156 qualified auditors already who represent 69 states and all ICAO regions. In: Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006, p 25
[33] Auditor Training and Certification In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/Training.htm
[34] The ICAO USAP Principles In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/USAP_Principles.htm
[35] Confidentiality: In:http://www.icao.int/cgi/goto_m_ atb.pl?icao/en/atb/asa/Confidentiality.htm
[36] Aviation Security Audit Section - Scope of Audits, http://www.icao.int/cgi/goto_m_atb.pl7icao/en/atb/asa/AuditScope.htm
- 87/88 -
[37] Of course the needed time is determined, influenced by the size of the airport, its complexity and the number of audited airports.
[38] The Audit Process In: http://www.icao.int/cgi/goto_m_atb.pl?icao/en/atb/asa/Process.htm
[39] Security Implementation and Assistance Section (SIA)
[40] The process consisted of three main phases. First the leader of the monitoring group visited the country - which requested the audit - in order to be able to plan the process in the interest of bigger efficiency. After the supervision procedure an aviation security programme plan was worked out in point of the certain state - what is forwarded to it. After this - if it is necessary - the concerned persons are trained, but security devises are also purchased for states which can not afford them. In the third phase of the programme a security expert carries out a formal post-control - the corrective action plan and the success of the whole process is checked. In: Aleman, M. A.: Strengthened Aviation Security Branch Oversees Newly-Developed Assistance Programme, ICAO Journal, Vol. 45, No. 6., June 1990, p 9-10.
[41] ibid. p 9.
[42] Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006, p 26
[43] http://www.icao.int/cgi/goto_m_atb/fal/Passport_ concept.htm "One Person, One Passport Concept"
[44] In 1997 ICAO called on member states to keep from issuing common passport for spouses, both parties should possess an own one. In: ibid.
[45] On one hand it was considered to be too early because MRTDs are not widespread, on the other hand enough time should be assured for states to withdraw the common documents. In: ibid.
[46] MRTDs should be issued according to ICAO Doc 9303 which standardised the format of passports and the personal data which should be included.
[47] There were states where children and the spouse were included in the common passport, while in other countries none of these two groups "have won the status." The practice of states was not common in the fact either till what age children were included in the common passports. Personal data appearing in passports did not show a common picture either - there were countries where no data were recorded about the above mentioned persons at all. In: ibid.
[48] The Council of ICAO drew the attention to the possibility of misuse of passports in connection with committing certain crimes. The above mentioned crimes also belong to this category. In: ibid.
[49] Besides the rule was deleted from the text which called upon states not to demand a separate passport from children under the age of 16. Further the proposal -which required a separate passport for spouses - became a compulsory rule. In: ibid.
[50] According to the proposal preferences have to be ensured for families with more children, so issuing passport for children should cost less, than for adults, since they are valid for a shorter time because of the fast changing features, physical appearance of children. In: ibid.
[51] Article 22., 23., and 37. of Chicago Convention
[52] The so called Optical Character Recognition (B, OCR-B)
[53] To the common elements of regulations for documents belong the requirements for their physical appearance: resistance to chemicals, stability relating to temperature, building in appropriate security elements in order to eliminate their misuse and forgery. In: Doc 9303 http://www.icao.int/mrtd/publications/doc.cfm
[54] Safety and Security: The number of fatal accidents and fatalities rose significantly, sparkling a call for safety enhancement ICAO Journal, Vol. 61, No. 5., September-October 2006, p 26.
[55] About the possible use of biometrics, their comparison - see chart In: http://www.tml.tkk.fi/Opinnot/Tik-110.501/1998/papers/12biometric/biometric.htm#ch4
[56] According to an old saying security has three levels: "The lowest level of security is defined as something you have in your possession, such as an ID badge with a photograph on it. The second level of security is something that you know, such as a password used with computer login or PIN code to use your bank account card on ATM. The highest level of security is something what you are and something that you do. This is essentially what biometric technology is all about." In: Huopio, Simo: Biometric Identification, "Authorization and Access Control in Open Network Environment, http://www.tml.tkk/fi/Opinnot/Tik-110.501/1998/papers/12biometric/biometric.htm
[57] The famous machine with the name "Identimat" was applied at a Wall Streat investment company, the "Shearson Hamill". When identifying the machine measured the length of fingers and the shape of the hand. The installment worked till 1987. In: Yfantis, Konstantinos N., Applications of Biometrics Implications for Security and Ethics, University of Illionis at Urbana -Champaign, November 13, 1997, http://www.staff.uiuc.edu/~efantis/biometrics/sld001.htm
[58] HUOPIO p 4-5
[59] One possibility of its applying is guarding top secret documents with the help of computer systems. The face of the person sitting in front of the computer is the guarantee for elimination of unauthorized access to top secret information: as soon as it does not detect the authorized person's face e.g. it turns from the machine - data disappear from the screen. ibid. p 6.
[60] ibid.
[61] The relative position of minutiae of fingerprints is checked. According to empirical studies there are not two unique persons who have more than 8 common minutiae points. Other methods check the position of pores on fingers. Ibid.
[62] Pilots had positive feedback about applying the method in different projects.
[63] It happened in more cases that to get a good quality fingerprint with first hand has to be cleaned from impurities...
[64] Today the identification of palm prints has significance only because of images found on crime scenes, though several enterprises try to break in the market in connection with commercial utilization as well with the hope that they "step on the way of fingerprints".
[65] Identification by fingers is very similar to that of by the hand.
[66] Identification by human odour is under expansion recently. Usually sample is taken from wrist in order to minimize intrusion into private sphere. Use of DNS for this purpose is difficult, uneasy, expensive and takes a long time -(at least 10 minutes) and bothersome (you have to give blood and sample from the mouth).
[67] Biometrics Deployment of Machine Readable Travel Documents, ICAO TAG MRTD/NTWG, Technical Report, Development ans Specification of Globally Interoperable Biometric Standards for Machine Assisted Identity Confirmation Using Machine Readable Travel Documents, In: http://www.icao.int/mrtd/down is load/documents/ Biometrics deployment of Machine Readable Travel Documents 2004.pdf, 21 May 2004, Biometric Selection Report, TAG, February 2002
[68] Gilenson, Hughes: Holistic Approach to Document Security Beginning to Take Hold In: ICAO Journal, Vol. 59 No. 7., October 2004, p 15., 25
[69] ibid. p 25
[70] In Chicago at O'Hare airport trailer and truck drivers are identified by their fingerprints in the interest of cargo security. The practice proves that this makes identification twice-four times faster. At Douglas airport and at US Airlines personnel get admission to certain areas. In: Atkinson, Robert D.: Aviation Security System for 21st Century Must Fully Incorporate Latest Technologies, ICAO Journal, Vol. 57 No. 5., June 2002, p 19.
- 88/89 -
[71] ibid. p 30.
[72] Irma van der Ploeg: Biometric Identification Technologies: Ethical Implications of the Informatization of the Body, Biometric Technology and Ethics, BITE Policy Paper No. 1, March 2005. In: www.danishbiometrics.org/admin/files/policy_paper_1_july_version.pdf
Lábjegyzetek:
[1] The Author is a PhD-student.

